
The Data Protection Act: Your Quick Compliance Guide

Jamaica’s Data Protection Act has shifted privacy from “good practice” to a board level compliance issue. The fastest way to get control is to treat it like a governance programme, not a one time policy update. This quick guide is designed for busy leaders who need to understand what matters, what evidence to build, and what to fix first.
The Data Protection Act in one minute (what it expects from your organisation)
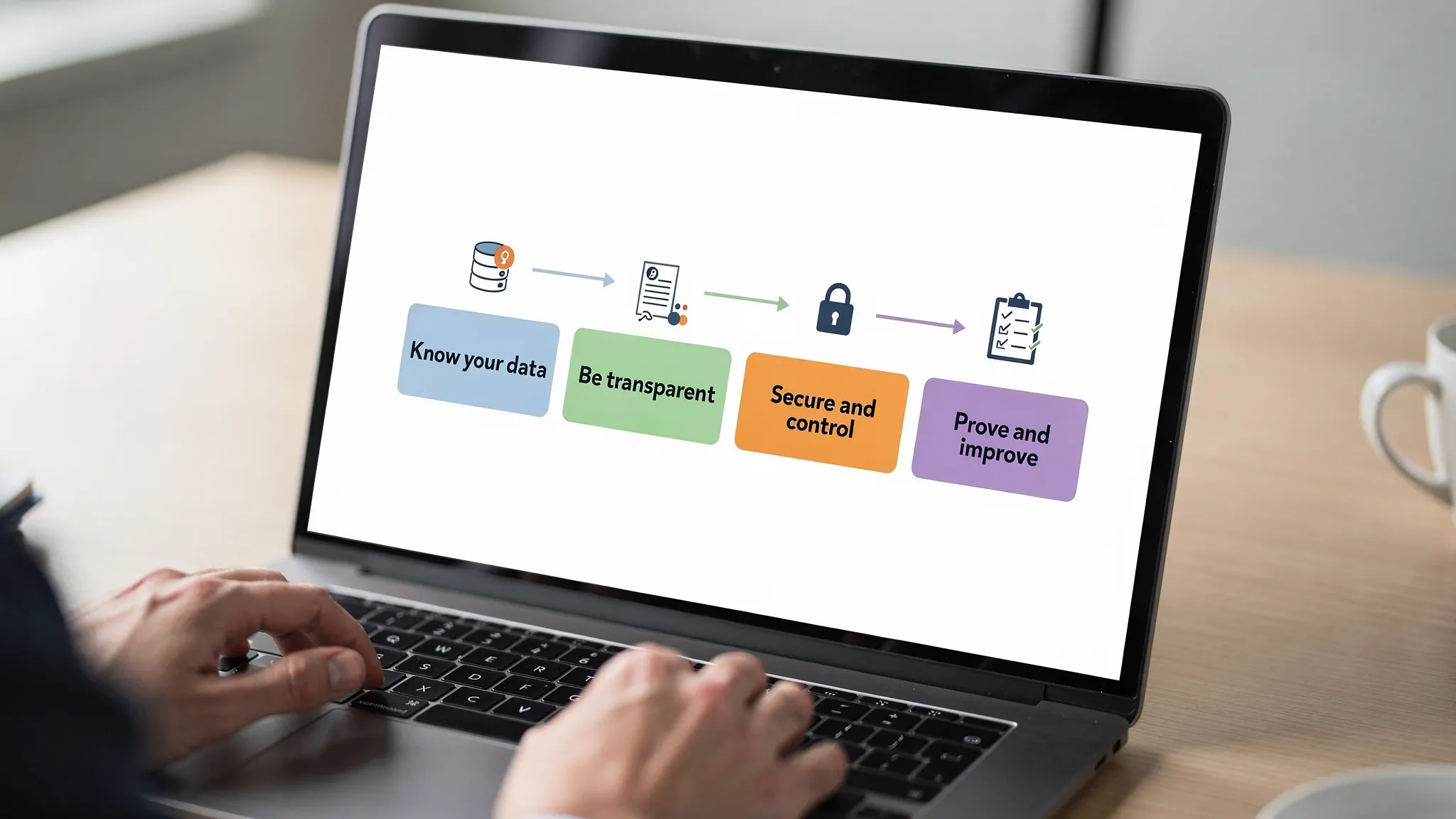
At a practical level, compliance comes down to four outcomes:
You know what personal data you have, where it lives, and why you have it.
You can explain your processing clearly to people (privacy notices) and honour their rights.
You protect data with proportionate security and manage vendors who touch your data.
You can prove it with documents, records, and repeatable processes (accountability).
If you want a deeper foundation before you start implementing, PLMC has supporting reads on data privacy principles and rights in Jamaica and a longer Jamaica Data Protection Act guide for businesses.
Your quick compliance map (what to do, what to keep as evidence)
Use the table below as a “minimum viable compliance” target. It also helps you brief your executives on what you can show clients, regulators, and auditors.
Compliance area | What “good” looks like | Evidence you should be able to produce |
Data inventory and flows | A living view of systems, data types, purposes, recipients, storage locations, and retention | Data inventory (spreadsheet or tool output), high level data flow diagram, system list |
Lawful and fair processing | Each key activity has a documented reason for processing and aligns with stated purpose | Processing register, purpose statements, intake forms that collect only what’s needed |
Transparency (privacy notices) | Notices are clear, accurate, and match reality (web, HR, customer touchpoints) | Published privacy notices, internal notice templates, version history |
Individual rights handling | Requests are triaged, verified, logged, and fulfilled within legal timeframes | Rights request procedure, request log, response templates |
Security and access control | Access is role based, monitored, and reviewed, data is protected in storage and transit | Access review records, security policies, incident/breach playbook |
Vendor and cloud management | Contracts reflect data protection responsibilities and vendors are risk assessed | Vendor due diligence checklist, DP clauses, vendor register |
Retention and disposal | Data is kept only as long as needed, then securely disposed | Retention schedule, disposal records, backup handling approach |
Training and awareness | Staff know what personal data is, how to handle it, and how to escalate issues | Training attendance records, role based training plan, awareness materials |
Step 1: Confirm your role and scope (controller vs processor)
Before you write policies, confirm how the Act applies to you in practice.
If your organisation decides why and how personal data is used (for example, a bank, school, clinic, retailer, employer), you are typically acting as a controller for those activities.
If you process personal data on behalf of another organisation (for example, payroll services, hosted IT providers, marketing agencies), you may be a processor for those activities.
Many Jamaican organisations are both. This matters because it determines what you must document, what you must tell people, and what you must require from vendors.
Step 2: Build a “good enough” data inventory (fast, then improve)
A data inventory is the quickest way to reduce risk because it reveals shadow systems, unnecessary collection, and unmanaged sharing.
Start with the data that creates the most risk if mishandled:
Employee and applicant records (HR)
Customer identity and contact details
Financial information
Health information (including medical and testing information)
CCTV and security logs
Then capture, for each activity: purpose, where the data is stored, who can access it, who it is shared with, how long it is kept, and whether it leaves Jamaica (including via cloud services).
If your organisation handles medical or testing information, note that sensitive information needs extra care. PLMC previously covered confidentiality expectations in COVID-19 results and the Data Protection Act.
Step 3: Fix transparency quickly (privacy notices that match reality)
Many organisations have a privacy notice that looks fine, but does not match how the business actually operates. That gap is a compliance risk.
Do a “notice reality check” against:
Website forms (contact us, quote requests, newsletter sign ups)
HR onboarding and background checks
CCTV signage and visitor logs
Marketing activities (email, SMS, WhatsApp business messaging)
Vendor sharing (payroll, benefits providers, cloud CRM)
Aim for plain language, and make sure the notice explains the main purposes, who receives the data, how to exercise rights, and how to contact your organisation about privacy.
Step 4: Put a simple rights request process in place
You do not need a complex portal on day one. You do need consistency.
A workable rights handling process typically includes:
A single intake channel (email address and backup phone contact)
Identity verification rules (proportionate to the request)
A request log (date received, type of request, owner, deadline, outcome)
Response templates (grant, partial grant, refusal where permitted)
A way to search and retrieve data across systems
This protects the organisation and the individual, and it reduces panic when a request comes in from a customer, employee, or client.
Step 5: Focus security on access, sharing, and vendor risk
Privacy compliance fails most often through basic operational weaknesses, not advanced hacking.
Prioritise three controls that reduce incidents quickly:
Access control (who can see what)
Tighten permissions in HR systems, shared drives, accounting tools, and CRMs. Document access approvals and review access periodically.
Secure sharing (how data leaves the organisation)
Set rules for emailing files, using USB drives, printing, and sharing via consumer apps. Use approved tools and keep audit trails where possible.
Vendor management (who else touches your data)
List vendors who store or access personal data (IT support, payroll, cloud platforms, call centres, marketing providers). Confirm contracts include data protection responsibilities and incident escalation expectations.
If you want a structured way to identify gaps, PLMC’s privacy and data protection practical checklist is a useful working document.
Department specific quick wins (what to fix first)
A fast programme works best when each function owns its high risk workflows.
HR
HR teams usually hold the most sensitive dataset in the organisation.
Restrict access to employee files and medical information
Review what you collect during recruitment and onboarding (collect only what is necessary)
Align your internal privacy notice with actual HR processes
Marketing and Sales
Marketing issues often come from unclear consent practices and unmanaged contact lists.
Document your basis for sending messages and keep proof where required
Stop importing contact lists that lack clear provenance
Make opt out and preference management easy, and honour it consistently
IT and Security
IT enables compliance, but also creates risk if systems are unmanaged.
Identify where personal data is stored (including email and shared drives)
Ensure backups are protected and access is controlled
Create an incident response playbook that includes privacy escalation
Procurement and Finance
Procurement is where vendor risk starts.
Add data protection checks to vendor onboarding
Maintain a vendor register for any service that touches personal data
Ensure contracts cover confidentiality, security expectations, and breach notification requirements
The “compliance evidence pack” you should keep ready
When clients, partners, or internal audit ask “are we compliant?”, the most credible answer is a set of documents you can show.
Keep a basic evidence pack that includes:
Data inventory and retention schedule
Privacy notices (customer and employee)
Policies (privacy, retention, acceptable use, incident management)
Rights request procedure and log
Vendor register and contract clauses
Training records
Risk assessments for high risk projects (for example, new systems or large scale monitoring)
For organisations planning a year of structured work, PLMC also publishes an implementation focused compliance roadmap for 2026.
Common mistakes that slow compliance (and how to avoid them)
Treating privacy as a legal document exercise
Policies help, but compliance is operational. If staff do not know how to handle a rights request or a suspected breach, the programme will fail.
Trying to map every dataset before taking any action
Start with high risk activities and core systems. Improve inventory coverage over time.
Ignoring vendors and cloud services
If a vendor mishandles data, your organisation may still carry reputational and contractual fallout. Vendor due diligence and contract controls are not optional.
Over collecting data “just in case”
Data minimisation is both a legal and a security strategy. If you never collected it, you cannot lose it.
Frequently Asked Questions
Is the Data Protection Act only for large companies? No. Any organisation handling personal data should take compliance seriously. The practical approach and scale of controls should match your size, risk, and processing activities.
Do we need a privacy notice even if we only collect basic contact information? Yes. If you collect personal data, you should be transparent about what you collect, why you collect it, who you share it with, and how people can exercise their rights.
What should we do first if we suspect a data breach? Contain the incident, preserve evidence, escalate internally to the responsible lead, and follow your incident response plan. Your next steps should include assessing impact, documenting what happened, and meeting any reporting and notification obligations within the relevant legal timeframes.
How do we handle employee medical information or test results? Treat it as highly sensitive data. Limit access, share only on a need to know basis, document your purpose and authority for processing, and ensure secure storage and retention controls.
What is the fastest way to show progress to management? Build a simple evidence pack: data inventory, privacy notices, rights request process, vendor register, incident playbook, and training records. Then track remediation actions against the highest risk gaps.
Need a fast, defensible compliance plan for your organisation?
PLMC supports organisations in Jamaica with Data Protection Act implementation, privacy awareness training, and broader governance, risk, and compliance integration. If you want help turning this quick guide into a working programme (with practical templates, risk prioritisation, and stakeholder training), request a free consultation and we will help you map a clear path from “we are trying” to “we can prove it.”
