
Jamaica Data Protection Act Explained for Businesses

Many Jamaican organisations only think about privacy when a customer complains, a laptop goes missing, or a vendor asks for a “DPA clause” in a contract. The Jamaica Data Protection Act changes that mindset. It sets clear rules for how businesses collect, use, share, secure, and retain personal data, along with rights for individuals and enforcement powers for the regulator.
This guide explains what the Act is aiming to achieve, what it typically means in day-to-day business operations, and the practical steps you can take to reduce risk and demonstrate compliance.
What the Jamaica Data Protection Act is designed to do
At its core, the Jamaica Data Protection Act establishes standards for responsible handling of personal data. For most businesses, that translates into three operational expectations:
Know what data you have (and why you have it).
Use it lawfully and transparently (including proper notices and controls).
Protect it (with appropriate security, governance, and vendor oversight).
A useful way to think about the Act is that it makes privacy a management system, not a one-time policy document.
For the exact legal wording, definitions, and duties, refer to the legislation and related guidance from Jamaican authorities, starting with the Jamaica Laws Online portal.
Does the Act apply to your business?
In practical terms, the Act will matter to most organisations that handle identifiable information about individuals in the course of business, including:
Employers handling staff records (payroll, performance, medical information, benefits)
Retail and e-commerce operations handling customer accounts and delivery details
Financial services and credit-related businesses handling KYC and transaction data
Healthcare and wellness providers handling health data
Schools and training institutions handling student records
Hospitality businesses handling reservations, CCTV, and incident logs
Any organisation using cloud services, outsourced support, marketing platforms, or CCTV
Even if you are a small or medium-sized enterprise, privacy obligations can still apply if you process personal data. The biggest difference is usually the scale of controls expected, not whether controls are needed at all.
Key concepts businesses should understand (in plain language)
Personal data
Personal data is information that can identify a person directly or indirectly. Examples include:
Names, TRN, passport number, driver’s licence number
Phone number, email address, home address
Employee ID, customer account numbers
CCTV footage where people are identifiable
Device identifiers and online identifiers where they can be linked to a person
Sensitive personal data (higher-risk data)
Most data protection laws treat certain categories of data as more sensitive, and therefore subject to stronger safeguards. While you should confirm the Act’s exact categories, this generally includes information such as:
Health and medical information
Biometric identifiers (for example, facial recognition templates)
Information revealing religious beliefs or political opinions
Sexual life or sexual orientation
Criminal allegations or convictions (where applicable)
If your organisation handles this kind of information, you should plan for tighter access controls, clearer legal justification, and stronger retention and security practices.
Controller vs processor
Many compliance issues come from confusion about roles.
A controller decides why and how personal data is processed (for example, a retailer deciding to collect customer details for delivery).
A processor processes personal data on behalf of a controller (for example, a payroll provider or cloud helpdesk platform).
This distinction matters because controllers typically carry the main accountability burden, and processors must follow contractual and security requirements.
The “data protection principles” and how they show up in real operations
Data protection laws are usually built on a set of principles. You will see these show up in regulator expectations, audit questions, and vendor due diligence. Here is a business-friendly mapping of what these principles tend to require.
Principle (plain English) | What it means for a business | Common evidence a regulator or client may expect |
Be fair and transparent | People should not be surprised by how you use their data | Clear privacy notices, consent language where required, customer scripts, HR notices |
Collect for specific purposes | Do not collect data “just in case” | Documented purposes, data inventory, forms aligned to purpose |
Minimise collection | Collect what you need, not everything you can | Shorter forms, optional fields justified, periodic review |
Keep data accurate | Wrong data can harm people and expose you to complaints | Update processes, self-service updates, correction workflows |
Limit retention | Keep data only as long as necessary | Retention schedule, deletion logs, archival controls |
Respect individual rights | People can request access, correction, and other rights under the Act | Request procedure, response templates, identity verification steps |
Secure the data | Apply appropriate security measures | Access control, encryption, MFA, endpoint protection, incident response |
Be accountable | You must be able to prove compliance | Policies, training records, risk assessments, vendor contracts |
If you already comply with sector requirements (for example, AML, cybersecurity frameworks, or contractual security obligations), you can often reuse that work, but you will still need privacy-specific governance.
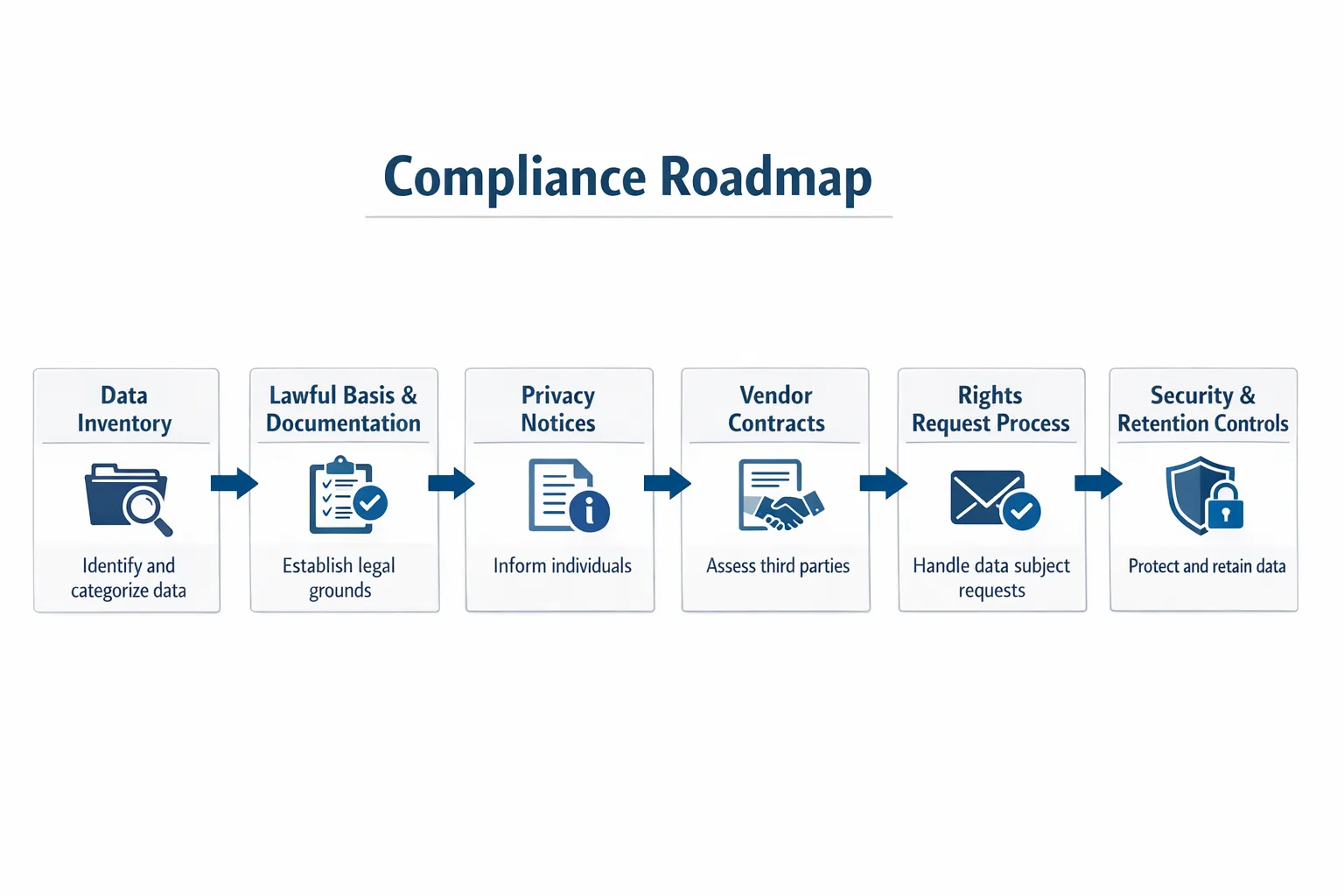
What businesses usually need to do to comply
Compliance is easiest when you treat privacy as a programme with owners, processes, and evidence. Below is a practical roadmap that works for most Jamaican organisations.
1) Build a data inventory (what you have, where it is, who has it)
Start by mapping personal data across:
HR (recruitment, payroll, disciplinary records)
Customers and marketing (CRM, mailing lists, loyalty programmes)
Operations (CCTV, visitor logs, incident reports)
Finance (invoices, credit notes, payment records)
IT (email, file shares, cloud drives, helpdesk)
Vendors (payroll services, cloud hosting, marketing platforms)
Output to aim for: a data register that lists the data types, purposes, systems, access roles, retention, and sharing.
2) Confirm your lawful basis and document your “why”
Most organisations process personal data for a mix of reasons, such as providing a service, meeting legal obligations, running payroll, preventing fraud, or marketing.
The Act sets conditions for lawful processing. In practice, you should be able to answer, for each major dataset:
Why do we need this data?
What legal condition are we relying on (for example, consent or another permitted basis under the Act)?
Who do we share it with, and why?
How long do we keep it?
If you cannot clearly justify a dataset, it is a signal to redesign the process and reduce risk.
3) Fix your privacy notices and internal communications
Transparency is one of the fastest ways to reduce complaints.
At minimum, most businesses need:
A customer-facing privacy notice (website, apps, printed forms)
An employee privacy notice (HR)
Short-form notices where data is collected (for example, CCTV signage and contest entry forms)
Notices should align with reality. If your notice says you do not share data, but your CRM syncs to a third-party email platform, that gap becomes an easy enforcement issue.
4) Put contracts around vendor and cloud processing
If a vendor touches personal data, your contract should address privacy and security expectations.
Common vendor relationships that require attention:
Payroll and HR platforms
Email marketing tools
Customer support systems
Cloud storage and backups
IT managed service providers
Security monitoring providers
n Your contracts should reflect your controller/processor relationship and clarify responsibilities for security measures, breach notification, sub-processors, and data return or deletion at the end of the service.
5) Implement a rights request process (DSAR-ready)
Individuals typically have rights under data protection law (for example, to request access to their personal data and to request corrections). Even if requests are rare now, they can quickly become frequent once a business is known to be unprepared.
A basic rights request workflow includes:
A single intake channel (email address or form)
Identity verification steps
A search process across systems
A review step (to protect third-party data and confidential information)
Response templates and timelines
6) Align security controls with privacy risk
Security is a major part of privacy compliance, but privacy is not only security. Aim for “appropriate” controls based on the sensitivity and volume of personal data.
Common controls that support compliance:
Access control based on role (least privilege)
Multi-factor authentication for email and cloud tools
Encryption for laptops and backups
Secure disposal for paper records and old devices
Logging and monitoring for key systems
A tested incident response plan
If you handle sensitive personal data (for example, health-related data), stronger controls are usually expected.
7) Create a retention schedule and actually follow it
Many businesses keep records forever because deletion feels risky. Under data protection standards, indefinite retention is often hard to justify.
A workable approach is:
Document retention periods by record type (HR, customer, CCTV, finance)
Link retention to legal requirements and operational needs
Automate deletion where possible
Keep an exception process for litigation holds and investigations
8) Train your staff and keep training records
Privacy failures are frequently people-and-process failures, not technology failures.
Training should be role-based:
Frontline staff: scripts, ID verification, handling access requests
HR: employee data handling, recruitment data retention, references
IT: access management, incident handling, vendor reviews
Management: accountability, reporting, risk acceptance
Training records matter because they demonstrate accountability.
Data breaches: what changes under a data protection law
A breach is not only a hacker event. It can include:
Sending a customer spreadsheet to the wrong recipient
Losing an unencrypted phone with staff WhatsApp exports
Exposing CCTV footage to unauthorised persons
A vendor misconfiguration that makes files publicly accessible
The Act provides a legal framework for how breaches are handled, and regulators typically expect organisations to have an incident response capability that covers:
Containment and investigation
Risk assessment (harm to individuals)
Notification decision-making (regulator and affected persons, where required)
Corrective actions and lessons learned
If you do not have a documented incident response plan, it is difficult to show that you acted responsibly under pressure.
Cross-border data transfers (including cloud services)
Many Jamaican businesses use tools hosted outside Jamaica (email services, CRM platforms, payroll systems, cloud backups). Data protection laws often restrict transferring personal data overseas unless certain conditions are met.
Practical steps that reduce cross-border risk:
Know where your vendors store and process data
Ensure contracts include appropriate transfer and security clauses
Limit what you upload (data minimisation)
Apply encryption and strong access controls
If your organisation uses multiple cloud services, a vendor risk assessment process becomes essential.
A practical compliance checklist for Jamaican organisations
Use this as a starting point for internal planning.
Assign internal ownership (privacy lead and executive sponsor)
Create or update a data inventory and data flow map
Review collection points (forms, web pages, CCTV signage)
Update privacy notices (customers and employees)
Review vendor contracts and data sharing
Implement a rights request process and templates
Document retention rules and implement deletion
Implement security controls appropriate to risk
Train staff and keep evidence of training
Run a tabletop exercise for breach response
If you are regulated in other areas (for example AML compliance or cybersecurity expectations), integrate privacy into those governance processes so it is not a parallel programme.
Frequently Asked Questions
Is the Jamaica Data Protection Act the same as GDPR? It is not the same law, but it shares similar concepts such as personal data, transparency, accountability, and individual rights. If your organisation has done GDPR work (especially around notices, rights requests, and vendor contracts), you may be able to reuse parts of it, but you still need to map requirements to Jamaica’s Act.
What counts as personal data in a Jamaican business setting? Personal data generally includes any information that identifies a person (name, contact details, identifiers, CCTV images) or that can reasonably be linked back to an identifiable individual.
Do we need customer consent for everything? Not always. Data protection laws typically allow processing under several legal conditions, with consent being only one option. Your business should identify which condition applies to each processing activity and document it.
What should we do first to get compliant? Start with a data inventory and fix transparency (privacy notices and collection scripts). Those two steps quickly reveal gaps in purpose, retention, vendor sharing, and security.
Do small businesses have to comply? If a business processes personal data, it may have obligations under the Act. Smaller organisations often implement simpler controls, but they still need basic governance, transparency, and security.
Get help implementing a practical privacy programme in Jamaica
If you want support turning the Jamaica Data Protection Act into a workable, audit-ready programme, Privacy & Legal Management Consultants Ltd. (PLMC) can help with data protection implementation, privacy awareness training, risk assessments, and broader Governance, Risk, and Compliance integration.
You can start with a free consultation via Privacy & Legal Management Consultants Ltd. to discuss your current privacy posture and the most sensible next steps for your organisation.
