
Data Protection Basics: What Jamaican Firms Must Know

For many Jamaican organisations, “data protection” still sounds like a policy document you update once a year. In reality, it is a day-to-day business discipline that affects how you collect customer details, manage employee records, run marketing campaigns, use cloud tools, and respond when something goes wrong.
Jamaica’s Data Protection Act sets expectations for how organisations handle personal information, and it is increasingly common for clients, partners, and regulators to ask: “How do you protect data, and can you prove it?” This guide breaks down the essentials Jamaican firms should understand, and what “good” looks like in practice.
Why data protection matters for Jamaican firms (beyond avoiding trouble)
Data protection is not only a legal issue. It is also:
A trust issue: Customers are more cautious about sharing information when scams and identity fraud are common.
A revenue issue: Corporate clients and international partners often require privacy and security assurances before signing contracts.
An operational issue: Poor data handling leads to duplicated records, messy systems, preventable incidents, and slower customer service.
If your organisation handles employee files, customer databases, CCTV footage, delivery addresses, call recordings, online forms, loyalty programmes, or even WhatsApp order chats, you are already in “data protection territory.”
The legal baseline: understand the Data Protection Act
Jamaica’s Data Protection Act establishes rules for the collection, use, storage, and sharing of personal information, along with rights for individuals and oversight by the regulator.
To stay accurate on the exact wording and current commencement details, rely on primary sources:
The Data Protection Act on the Jamaica Laws website (search “Data Protection Act”).
Updates and guidance from the Office of the Information Commissioner (Jamaica) (where applicable).
This article is educational, not legal advice. The right approach for your firm depends on your data, systems, and risk profile.
Data protection basics: the key terms you must get right
A lot of compliance confusion starts with definitions. Get these clear early, because they affect your contracts, policies, and internal responsibilities.
Term | Plain-English meaning | Common Jamaican business examples |
Personal data | Information that identifies (or can identify) a person | Name, TRN, phone number, email, address, staff ID |
Sensitive personal data (or special category data) | Higher-risk personal info that needs stronger protection | Health information, biometrics, certain background checks (context matters) |
Data controller | The organisation that decides why and how personal data is used | Your company collecting customer sign-ups or HR records |
Data processor | A service provider handling personal data on your behalf | Payroll vendor, cloud HR system, outsourced call centre |
Processing | Almost anything done with personal data | Collecting, storing, emailing, analysing, deleting |
Data breach | Loss, unauthorised access, disclosure, or alteration of personal data | Mis-sent email, hacked mailbox, stolen laptop, exposed database |
One practical takeaway: if you use third-party tools (cloud email, CRM, accounting software, marketing platforms), you are likely a controller working with multiple processors. That means vendor due diligence and contract controls matter.
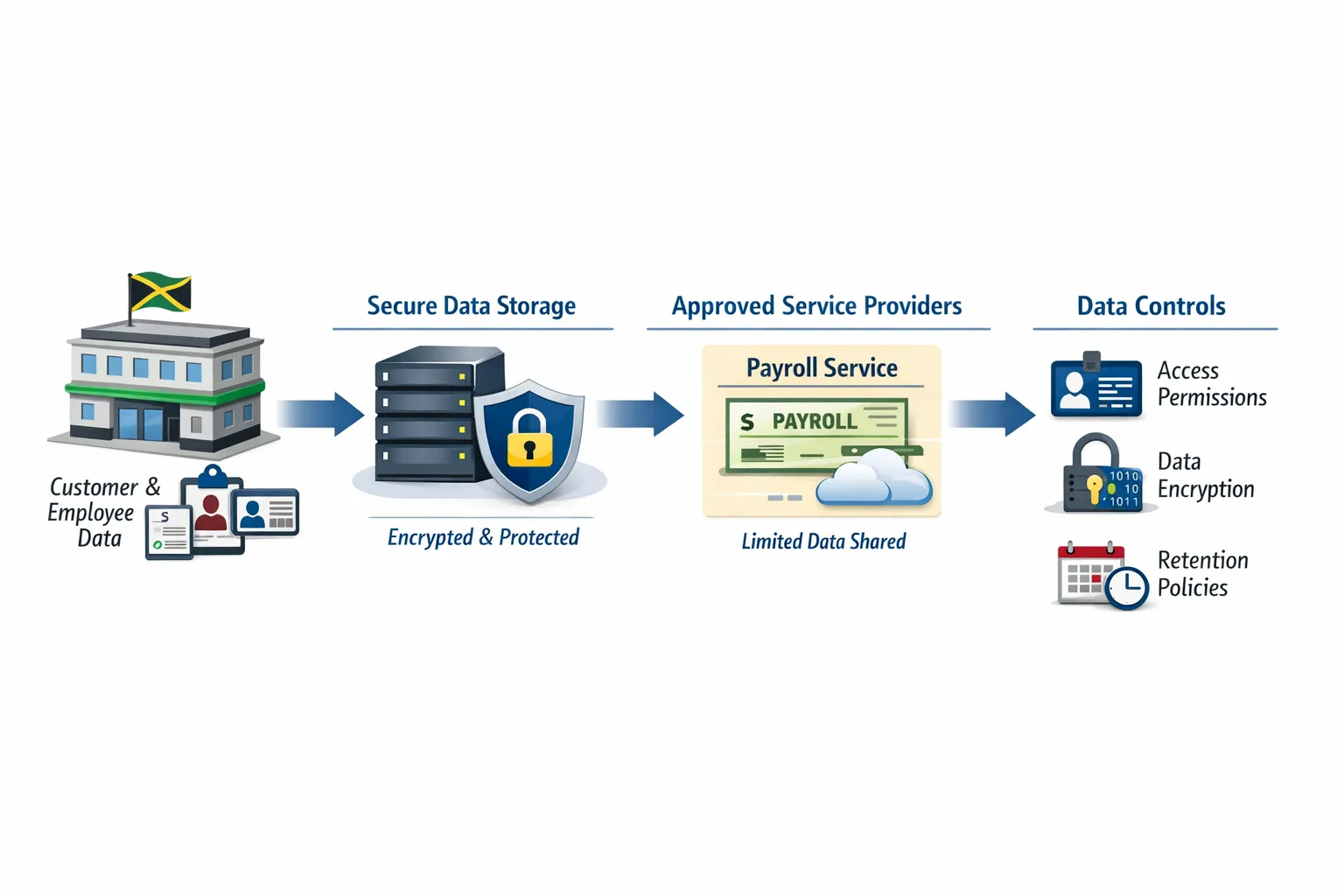
The core obligations Jamaican organisations should operationalise
Most data protection laws share common “fair handling” principles. The Data Protection Act expects organisations to handle personal information responsibly, transparently, and securely.
Here is what that looks like as business practice.
1) Be clear on what you collect, and why you collect it
A frequent compliance problem is collecting information “just in case.” The safer approach is data minimisation: collect what you need for a clear purpose.
Practical examples:
If you need an email address to send a receipt, do you also need date of birth?
If a form asks for TRN, can you explain why it is required, and who will access it?
If you record calls, can you justify the purpose (quality, security, training) and set a retention period?
2) Provide meaningful privacy notices
People should not have to guess what will happen to their information.
A strong privacy notice typically explains:
What data you collect
Why you collect it (purposes)
Who you share it with (categories of recipients)
How long you keep it (or how you decide)
How people can exercise their rights
How to contact your organisation about privacy
This should appear at the point of collection (web forms, onboarding packs, job applications), not buried after the fact.
3) Choose an appropriate legal basis (and do not over-rely on consent)
Many firms treat consent as the only option. Consent can be valid in some situations, but it must be genuine, informed, and easy to withdraw. In employment and certain service relationships, consent may be questioned if the individual cannot realistically say “no.”
A more mature approach is to document the justification for each processing activity (for example, to deliver a service, meet a legal obligation, or support legitimate business operations), and reserve consent for scenarios where it truly fits (like optional marketing preferences).
If you are unsure, this is a strong reason to do a structured assessment with a privacy professional.
4) Implement access control and “need-to-know” handling
In many organisations, data leakage is not caused by hackers. It is caused by overbroad access.
Focus on:
Role-based access (HR data visible to HR, not the whole office)
Removing access promptly when staff change roles or leave
Strong authentication for email and business systems
Logging and monitoring for sensitive systems where feasible
If you only do one technical improvement this quarter, consider turning on multi-factor authentication for business email and cloud systems.
5) Secure storage, safe sharing, and controlled devices
Basic security expectations include:
Encrypting laptops and mobile devices used for work
Avoiding personal email accounts for business files
Using approved file-sharing platforms rather than sending sensitive files openly
Applying secure disposal for physical records (locked bins, shredding)
For regulated or higher-risk data (financial, health-related, identity information), your security controls should be stronger and documented.
For practical security guidance that aligns with international best practice, you can also reference the NIST Cybersecurity Framework as a useful baseline.
6) Retention and disposal: keep data only as long as necessary
“Unlimited storage” has created a risky habit of keeping everything forever.
A defensible approach includes:
A retention schedule (by record type)
A process for secure disposal (digital and physical)
Clear ownership (who approves deletion, who executes it)
Retention decisions should consider legal requirements, operational needs, and risk. If you cannot justify why you still have it, you should not keep it.
7) Vendor and outsourcing controls (processors)
If a service provider processes personal data for you, your risk travels with them.
At minimum, your organisation should:
Conduct due diligence before onboarding vendors
Confirm where data is hosted (especially if outside Jamaica)
Use contracts that set privacy and security obligations
Ensure you can get data back and delete it at contract end
This is especially important for payroll, HR platforms, CRM systems, managed IT providers, and marketing agencies.
Individual rights: prepare for requests before the first request arrives
The Data Protection Act provides individuals with rights over their personal information. In practice, Jamaican organisations should be ready to receive and respond to requests such as:
Access to personal data held about them
Correction of inaccurate information
Objection to certain uses (depending on context)
Even if you have never received a request, you should build a simple process:
A dedicated email address or contact route
A method to verify identity (to prevent wrongful disclosure)
An internal workflow to locate data across systems
Response templates and tracking
The biggest operational obstacle is not the legal response, it is locating data that lives across email inboxes, spreadsheets, shared drives, and vendor platforms. Data mapping solves this.
Cross-border data transfers and cloud services: what to watch
Many Jamaican firms use overseas cloud services for email, accounting, HR, and storage. This can be compliant, but you must manage it.
Focus on three realities:
Your obligations do not disappear because data is in the cloud.
You should know where data is stored and accessed, including support access.
Contracts and controls matter, especially for sensitive or high-volume data.
Ask vendors:
Where is data hosted, and can you choose the region?
What security measures are standard (encryption, MFA, monitoring)?
How do you handle breaches, and how quickly do you notify customers?
Can you support retention controls and deletion requests?
Data breaches: build readiness, not panic
A breach response is not only an IT issue. It involves HR, legal, communications, and leadership.
A practical, business-friendly incident response capability includes:
A clear internal reporting channel (staff must know who to tell)
A triage process (what happened, what data, how many people, what harm)
Steps to contain (disable accounts, reset credentials, isolate devices)
Evidence preservation (do not “wipe and hope”)
A decision-making process for notifications and communications
Even a “small” incident like an email sent to the wrong recipient can be a serious privacy event depending on what was shared.
A simple starter plan for Jamaican firms (30 to 90 days)
If you are starting from scratch, aim for progress you can defend, not perfection.
Timeframe | What to implement | What you gain |
First 30 days | Data inventory, key policies draft, basic access review, MFA for email, identify key vendors | Immediate risk reduction and visibility |
31 to 60 days | Privacy notices, vendor contract updates, retention schedule outline, staff awareness sessions | Fewer compliance gaps and better consistency |
61 to 90 days | Incident response tabletop exercise, rights request workflow, risk assessment for high-risk processing | Operational readiness and audit confidence |
If your organisation processes higher-risk data (children’s data, health data, identity documents at scale, financial profiling), you should prioritise a structured risk assessment early.
Common gaps we see in Jamaican organisations
These issues are fixable, but they tend to cause the most trouble during audits, partner due diligence, or incidents.
Common gap | Why it is risky | What “good” looks like |
No data map | You cannot respond quickly to breaches or rights requests | A living inventory of systems, data types, owners, vendors |
Informal sharing (WhatsApp, personal email) | Data leaks, poor access control, no retention | Approved channels, guidance, and enforcement |
Weak vendor oversight | Third parties become your weakest link | Due diligence, contracts, periodic reviews |
No retention rules | “Forever data” increases breach impact | Retention schedule and routine disposal |
Training is ad hoc | Staff mistakes repeat | Role-based privacy training with refreshers |
How PLMC can support your data protection programme
Privacy and compliance work best when it is practical, documented, and aligned with your organisation’s real operations.
Privacy & Legal Management Consultants Ltd. (PLMC) supports Jamaican organisations with:
Data protection implementation aligned to the Data Protection Act
Risk assessment tools and governance frameworks
Training sessions to build privacy awareness across teams
Broader GRC integration, including cyber security, corporate governance, and compliance support
If you need a starting point, a scoping session can help clarify your obligations, risks, and next steps.
Frequently Asked Questions
Does the Data Protection Act apply to small businesses in Jamaica? Yes, in many cases. Size is not the only factor. If you collect and use personal information about customers, staff, or members of the public, you should assume data protection obligations apply and then confirm specifics based on your activities.
What counts as personal data in a Jamaican workplace? Common examples include employee files, emergency contact details, performance notes, payroll information, ID copies, and even email content if it identifies an individual.
Do we need consent for every use of customer data? Not necessarily. Consent is one possible legal basis, but many routine business activities rely on other lawful justifications. The key is to document your purpose, be transparent, and avoid using data in unexpected ways.
Is CCTV footage covered by data protection rules? In most contexts, yes. CCTV that can identify individuals is typically personal data. You should have signage, defined purposes, controlled access, and clear retention periods.
How long should we keep personal data? Keep it only as long as necessary for the purpose it was collected, considering legal and operational requirements. A retention schedule by record type is the most defensible approach.
We use overseas cloud services. Is that automatically non-compliant? Not automatically. Many organisations use overseas providers, but you must manage cross-border risks through vendor due diligence, contract terms, access controls, and clear handling procedures.
Get practical help with Jamaican data protection compliance
If you want a clear, structured path to meet Jamaica’s Data Protection Act expectations, PLMC can help you assess your current posture and prioritise fixes that reduce risk quickly.
Start with a conversation: visit Privacy & Legal Management Consultants Ltd. to request a consultation and explore resources for building a sustainable data protection programme.
